Part 1. Introduction.
Part 2. DBMail.
Part 3. Postfix.
Part 4. SASL.
Part 5. SPF. DKIM. DMARC. Clear headers. DNS PTR.
SPF
Sender Policy Framework is an email authentication method designed to detect forged sender addresses in emails (email spoofing). SPF allows the receiver to check that an email claiming to come from a specific domain comes from an IP address authorized by that domain’s administrators.
Add this record to your DNS server.
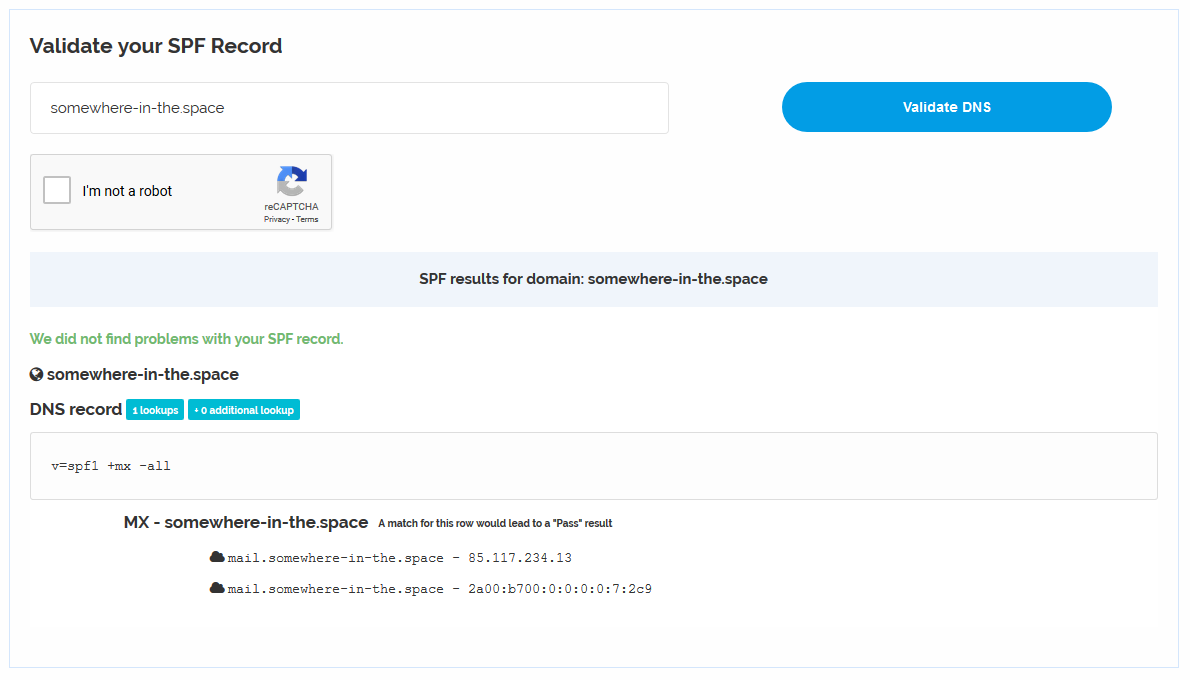
somewhere-in-the.space. IN TXT "v=spf1 +mx -all"
Check SPF is working.
DKIM
DomainKeys Identified Mail is an email authentication method designed to detect forged sender addresses in emails (email spoofing). DKIM allows the receiver to check that an email claimed to have come from a specific domain was indeed authorized by the owner of that domain. It achieves this by affixing a digital signature, linked to a domain name, to each outgoing email message.
Install opendkim.
apt-get install opendkim opendkim-tools
Create DKIM keys.
mkdir /etc/postfix/dkim/ opendkim-genkey -D /etc/postfix/dkim/ -d somewhere-in-the.space -s mail chmod 600 /etc/postfix/dkim/mail.private chown -R opendkim /etc/postfix/dkim/
Edit /etc/opendkim.conf file.
Syslog yes UMask 007 Mode sv Socket inet:8891@localhost PidFile /var/run/opendkim/opendkim.pid OversignHeaders From TrustAnchorFile /usr/share/dns/root.key UserID opendkim Canonicalization relaxed/relaxed X-Header yes KeyTable file:/etc/postfix/dkim/keytable SigningTable file:/etc/postfix/dkim/signingtable
Edit /etc/postfix/dkim/keytable file.
mail._domainkey.somewhere-in-the.space somewhere-in-the.space:mail:/etc/postfix/dkim/mail.private
Edit /etc/postfix/dkim/signingtable file.
somewhere-in-the.space mail._domainkey.somewhere-in-the.space
Edit /etc/default/opendkim file.
RUNDIR=/var/run/opendkim SOCKET="inet:8891@localhost" USER=opendkim GROUP=opendkim PIDFILE=$RUNDIR/$NAME.pid EXTRAAFTER=
Configure postfix to use opendkim. Add the following lines to /etc/postfix/main.cf file.
milter_default_action = accept milter_protocol = 2 smtpd_milters = inet:localhost:8891 non_smtpd_milters = inet:localhost:8891
Add the following DNS records. You can get a p value from /etc/postfix/dkim/mail.txt file. You may need to concat two parts of key if key is long enough.
cat /etc/postfix/dkim/mail.txt
mail._domainkey IN TXT ( "v=DKIM1; h=sha256; k=rsa; "
"p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA0myKECDtkhaMw158x3fNOwR3jF2DXAqg+ABiQ4bDOFewSY4zKXzKbBwvzcOYZLPzj6iwIK+aJJ3/siTJ3QQS7mbrzLw6smPIN/tDEm0xe0aNn4mzTrGROUUGgL0FXVLkJRNkiQXGA0aTAYk2prpFJihr/Sp+ZqFkxrpkOo23ylk0N0/bxHN3Rj9/epXYpWyPcLyMzggK1vC9K8"
"UhSZ8TfL/7E8n0zlEgxJ3AmoqaKCSPQKWB6F3dnt5RDp5Ev+8Wwq+M6Dn1/wpG5mp2qQMT8FsxIvPhdNKQFN3cfa1QFUHeSSZfgHr9ZTXxWYnOe8AlyFg1evNOCpNLCPIZk2A7mwIDAQAB" ) ; ----- DKIM key mail for somewhere-in-the.space
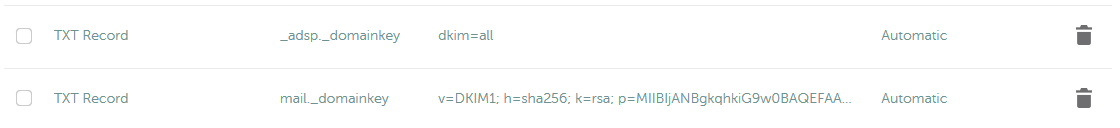
mail._domainkey.somewhere-in-the.space. IN TXT "v=DKIM1; h=sha256; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA0myKECDtkhaMw158x3fNOwR3jF2DXAqg+ABiQ4bDOFewSY4zKXzKbBwvzcOYZLPzj6iwIK+aJJ3/siTJ3QQS7mbrzLw6smPIN/tDEm0xe0aNn4mzTrGROUUGgL0FXVLkJRNkiQXGA0aTAYk2prpFJihr/Sp+ZqFkxrpkOo23ylk0N0/bxHN3Rj9/epXYpWyPcLyMzggK1vC9K8UhSZ8TfL/7E8n0zlEgxJ3AmoqaKCSPQKWB6F3dnt5RDp5Ev+8Wwq+M6Dn1/wpG5mp2qQMT8FsxIvPhdNKQFN3cfa1QFUHeSSZfgHr9ZTXxWYnOe8AlyFg1evNOCpNLCPIZk2A7mwIDAQAB" _adsp._domainkey.somewhere-in-the.space. IN TXT "dkim=all"
The second DNS record tells receiver to check mail signature for all incoming mails. ADSP is obsolete and replaced by DMARC, but we use it for backward compatibility.
Restart services.
systemctl restart opendkim systemctl restart postfix
Test DKIM key.
opendkim-testkey -d somewhere-in-the.space -s mail -vvv
opendkim-testkey: using default configfile /etc/opendkim.conf opendkim-testkey: checking key 'mail._domainkey.somewhere-in-the.space' opendkim-testkey: key not secure opendkim-testkey: key OK
Test DKIM working correctly sending a test mail to check-auth@verifier.port25.com.
echo "test" | mail -aFrom:admin@somewhere-in-the.space check-auth@verifier.port25.com
You will receive a mail with check results. The following line means DKIM check is passed.
### DKIM check: pass ###
DMARC
Domain-based Message Authentication, Reporting and Conformance is an email authentication protocol. It is designed to give email domain owners the ability to protect their domain from unauthorized use, commonly known as email spoofing. Once the DMARC DNS entry is published, any receiving email server can authenticate the incoming email based on the instructions published by the domain owner within the DNS entry.
Let’s tell mail servers to move spoofed mails to a spam folder and send a report about such mails to postmaster@somewhere-in-the.space.
Create the following DNS record.
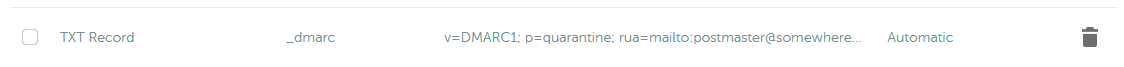
_dmarc.somewhere-in-the.space. IN TXT "v=DMARC1; p=quarantine; rua=mailto:postmaster@somewhere-in-the.space"
Check DMARC configured well.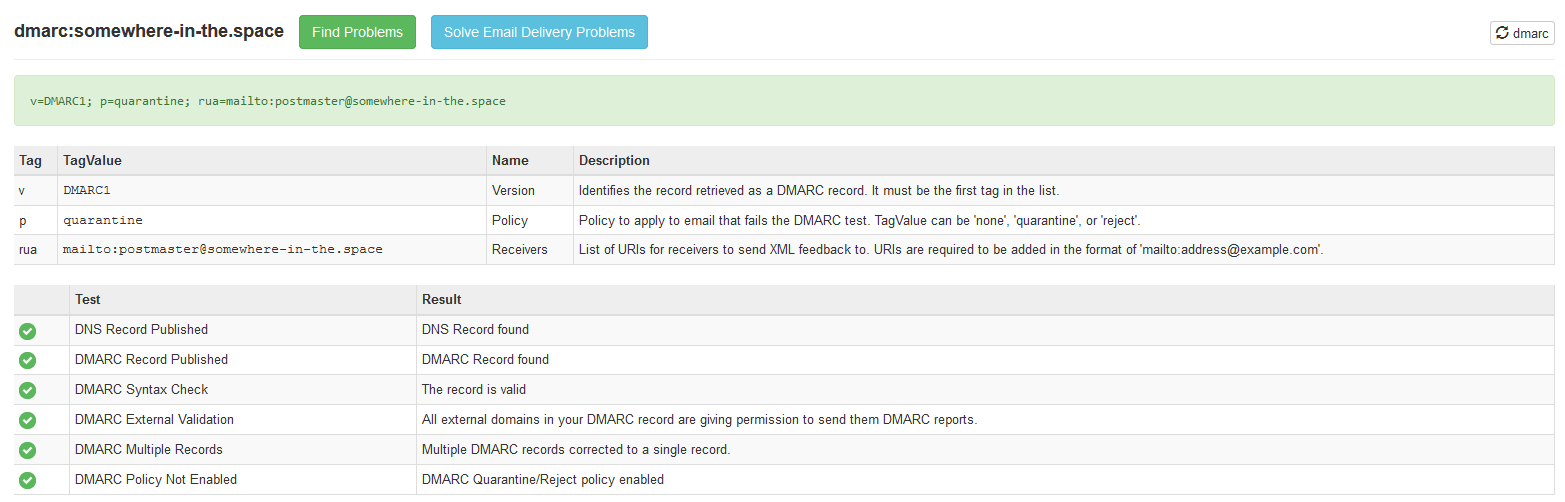
Clear headers
By default, postfix will not clear unnecessary mail headers out of your mail. It means, receiver will get info about your ip, machine name and client software. Besides, it can affect your spam score sometimes.
Install postfix pcre module.
apt install postfix-pcre
Add the following line to /etc/postfix/main.cf file.
header_checks=pcre:/etc/postfix/header_checks.pcre
Create /etc/postfix/header_checks.pcre file.
/^Received: .*/ IGNORE /^X-Originating-IP:/ IGNORE /^User-Agent:/ IGNORE /^X-Mailer:/ IGNORE /^X-PHP-Originating-Script/ IGNORE
Restart postfix.
systemctl restart postfix
DNS PTR
To keep your spam score good, you need to contact your hosting provider asking to create DNS reverse lookup records. This records should not be defined in your DNS server.
Check reverse records using dig command.
dig -x your-IPv4 dig -x your-IPv6
Spam score
Finally, check your spam score.
echo "Hello, my friend. How are you?" | mail -s "Hello" -aFrom:admin@somewhere-in-the.space test-rbjqd@mail-tester.com


Очень полезная информация!
Огромное спасибо за статью